Computer Security is very important nowadays, digital age, computer security is more important than ever. With the rise of cyber-attacks, data breaches, and online threats it’s crucial to take steps to protect your personal and sensitive information when you go online on the internet. Here are 10 essential computer security tips to keep your data safe and secure by following some steps. Remember that Computer Security is an ongoing process. It’s essential to stay vigilant, adapt to new threats, and practice these tips consistently to protect your personal and sensitive information online.
Here are the 10 Best Computer Security Tips to keep your Data safe when you are Online:
- Use Strong Passwords
- Keep Your Software Up to Date
- Be Wary of Suspicious Emails
- Use Antivirus and Malware Protection
- Backup Your Data
- Secure Your Network
- Use Two-Factor Authentication
- Limit Personal Information on Social Media
- Be Careful When Using Public Wi-Fi
- Educate yourSelf
Use Strong Passwords

What is a Strong Password – A strong password is a secure and difficult-to-guess combination of characters used to protect your online accounts, data, and computer security. It typically includes the following characteristics
- Length – A strong password should be relatively long, typically at least 12 characters. Longer passwords are generally more secure this will help you to protect your computer security.
- Complexity – “computer security” It should contain a mix of different character types, such as uppercase letters, lowercase letters, numbers, and special symbols (e.g., ! @, #, $).
- Unpredictability – Avoid using easily guessable information that you choose, such as common words, phrases, or patterns (e.g., “password,” “123456,” or “qwerty”). Instead of, using a combination of random characters.
- Uniqueness – It’s important to use a different password for each of your accounts to prevent a security breach on one account from compromising others in other ways “Do not use the same password for multiple accounts. If your one account is compromised, all of your accounts be at risk, and your computer security will be damaged”
- Avoiding common patterns – Steer clear of easily predictable patterns, like sequences of numbers or letters (e.g., “12345” or “abcdef”) this will hence your computer security.
- Regular updates – Change your passwords regularly to further enhance security. Strong passwords are essential for protecting your online accounts and information from unauthorized access and potential cyber threats. Additionally, using a password manager can help you generate and manage strong, unique passwords for each of your accounts in computer security.
Keep Your Software Up to Date for Computer Security

In computer security keeping your software up to date is one of the most important things you can do to protect your devices and data from security threats. Software updates often include security patches that fix known vulnerabilities that attackers could exploit. They can also improve performance and reliability, and add new features.
Here are some points on how to keep your software up-to-date:
- Enable automatic updates – Most software programs now offer automatic updates, which means that they will automatically download and install updates as soon as they are available. This is the easiest and most convenient way to keep your software up to date. It will help you to protect your computer security.
- Check for updates manually – If you don’t have automatic updates enabled, you should check for updates manually on a regular basis. This is especially important for your operating system, web browser, and other security-critical software. If you run the required talk on your computer your computer security will work smoothly.
- Use a patch management tool – If you have a lot of devices to manage, you may want to consider using a patch management tool. This can automate the process of checking for and installing updates on all of your devices, If your patch management tool works fine computer security will work well.
Here are some specific instructions for keeping your software up to date on different types of devices for computer security:
On Windows Computer:
- Go to Start > Settings button> Update & Security option> Windows Update.
- Click Check for Updates.
- If any Updates are available, click Install Now.
- On macOS Device
- Go to the Apple menu option > System Preferences > Software Update.
- Click Check for Updates.
- If any updates are available, click Update Now.
On Android Device:
- Go to Settings > System option > System Update.
- Tap Check for updates.
- If any updates are available, tap Download and Install.
On iOS:
- Go to Settings > “General” Option > Software Update.
- Tap Download and Install.
Third-party applications – (computer security) Most third-party apps have their own update mechanisms. You can usually check for updates by opening the app and going to the settings menu. It is important to note that not all software updates are created equal. Some updates may be more important than others, especially those that include security patches. It is a good idea to prioritize installing updates for security-critical software, such as your operating system, web browser, and antivirus software. You should also be careful about installing updates from unknown sources online. Only install updates from trusted sources, such as the software vendor’s website or the app store.
Be Wary of Suspicious Emails
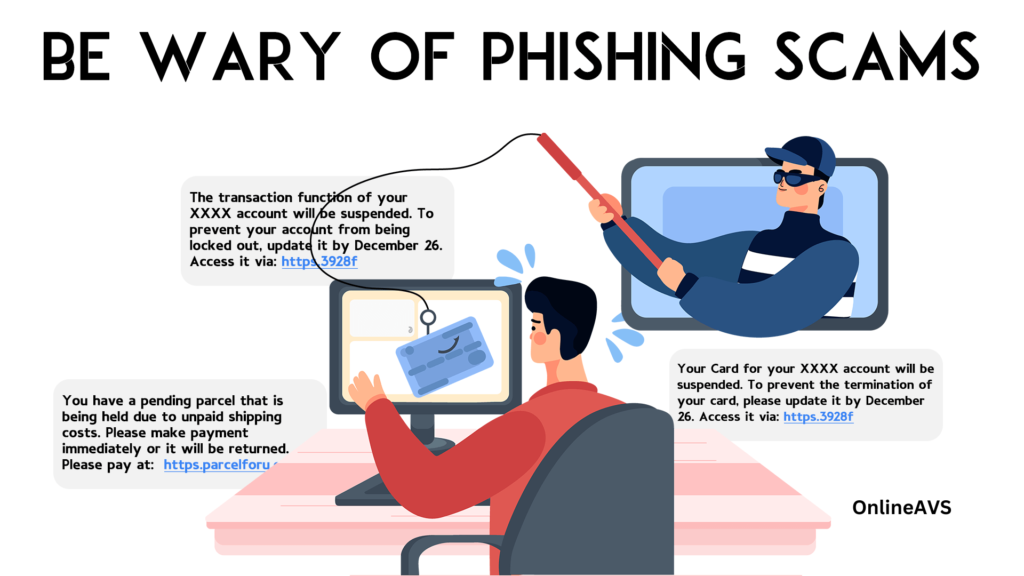
Phishing emails are a type of email scam that attempts to trick you into revealing sensitive information, such as passwords, credit card numbers, or Social Security numbers. Phishing emails can be very convincing, but there are some things you can do to protect yourself from falling victim to one.
Here are some tips on how to be wary of suspicious emails:
- Check the sender’s email address – Phishing emails often come from addresses that look like they’re from legitimate companies, but there are usually some small differences. For example, the email address might be spelled slightly differently, or it might use a different domain name (e.g., @gmail.com instead of @google.com).
- Hover over links before clicking on them – This will show you the actual URL of the link, which may be different from the URL displayed in the email. If the URL doesn’t look like it’s from the company that the email claims to be from, don’t click on it.
- Don’t open attachments from unknown senders – Attachments can contain malware that can infect your computer or steal your personal information.
- Be wary of emails that create a sense of urgency or offer something that seems too good to be true. Phishing emails often try to pressure you into acting quickly without thinking, or they offer something that seems too good to be true, such as a large sum of money or a free prize. If you receive an email that you think might be a phishing/scam email, the best thing to do is to delete it or block it without clicking on any links or opening any attachments. You can also report the email that you have got.
Here are some additional tips to Secure yourself and Computer security as well:
- set a strong email password and enable multi-factor authentication -This will make it more difficult for scammers to access your email account, even if they have your password.
- Keep your software up to date – Software updates often include security patches that can help protect you from phishing attacks and other online threats.
- Educate yourself about phishing scams. The more you know about phishing, the better equipped you’ll be to spot and avoid phishing emails.
“By following these tips, you can help protect yourself from phishing scams and keep your personal information safe.”
Use Antivirus and Malware Protection for Computer Security

(computer security) Antivirus and malware protection software works by scanning your computer for malware and removing it if it is found that will make your computer security better for work. Most antivirus software also includes real-time protection, which monitors your computer for suspicious activity and blocks malware before it can infect your system. There are many different antivirus and malware protection software products available, both free and paid. When choosing a product, it is important to consider the features that are important to you, such as real-time protection, malware removal, and parental controls. You can also follow this link to learn about NortonLifelock Security it will help you to secure your computer security and identity as well. You can follow this link to learn the Benefits of using Cyber security software in the Digital World
Here are some tips for using antivirus and malware protection software effectively:
- Install antivirus software on all of your computers and devices to get the best computer security.
- Keep your antivirus software up to date. Antivirus software vendors release regular updates to protect against new malware threats for your computer security.
- Run regular full scans of your computer. Even if you have real-time protection enabled, it is a good idea to run a full scan of your computer regularly to catch any malware that may have slipped through. This step will help you with your computer security.
- Be careful about what files you download from the internet. Only download files from trusted websites. If you are downloading files from an untrusted website your computer security will be damaged.
- Be careful about what emails you have opened and what links you click on. Phishing emails are a common way for malware to be spread. Once malware is spread in your computer then your computer security would be damaged.
- Be careful about what USB drives and other removable media you plug into your computer. These devices can also be used to spread malware to make infection for your computer security.
- By following these tips, you can help protect your computer security and devices from malware infection.
Backup Your Data
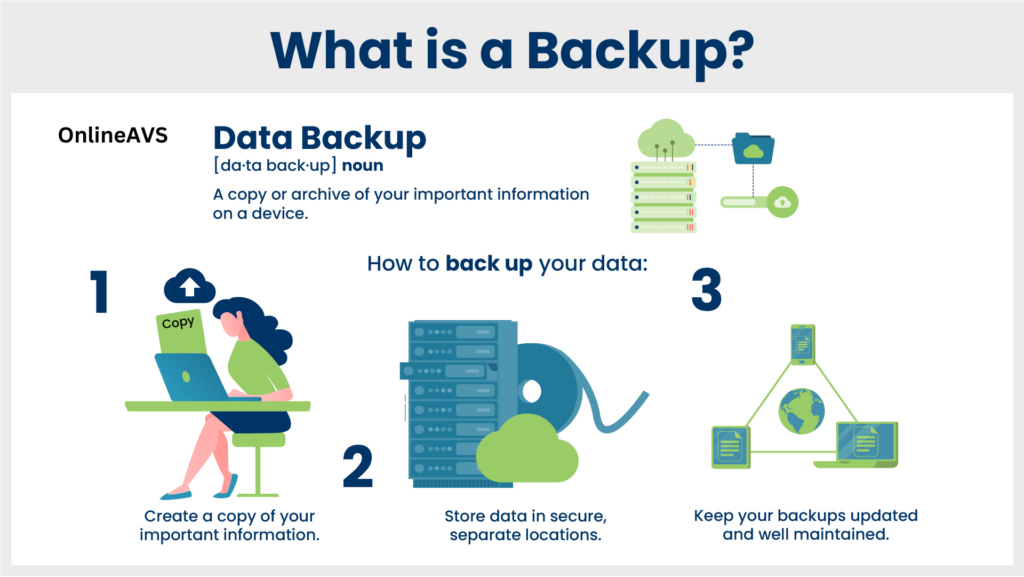
Backing up your data is the process of copying your data to a secondary location for preservation in case of equipment failure or catastrophe. This can include important files such as documents, photos, videos, and music, as well as system files and settings.
There are many different ways to back up your data, both locally and remotely. Some common backup methods include:
- External hard drives – External hard drives are a popular choice for backing up your data because they are relatively inexpensive and easy to use. Simply connect the hard drive to your computer and copy your data over to Hard Drives.
- Cloud storage – Cloud storage services such as Google Drive, iCloud, and Dropbox allow you to back up your data to a remote server. This can be a good option if you want to be able to access your data from anywhere or if you are concerned about losing your local backup in the event of a disaster.
- Network-attached storage (NAS) – NAS devices are dedicated storage devices that can be connected to your home or office network. NAS devices can provide a central location for backing up all of your devices on the network.
- Tape backup – Tape backup is a traditional backup method that is still used for large datasets and enterprise applications. Tape backups are typically more expensive than other backup methods, but they offer the advantage of being very durable and long-lasting.
“No matter which backup method you choose, it is important to back up your data regularly. This will help to ensure that you have a recent copy of your data in case of a loss.”
Secure Your Network

Securing your network is crucial to protect your data and devices from unauthorized access and potential cyber threats
There are many things you can do to secure your network, both at home and at work. Here are some tips:
- Use a firewall – A firewall is a network security device that can be hardware or software that monitors and controls incoming and outgoing network traffic. It can help to protect your network from unauthorized access, malware, and other threats. Most routers have a built-in firewall, but you may also want to consider using a dedicated firewall device.
- Use strong passwords and two-factor authentication (2FA) – Strong passwords are at least 12 characters long and include a mix of upper and lowercase letters, numbers, & symbols. You should also change your passwords regularly and avoid using the same password for multiple accounts because it can cause trouble. 2FA adds an extra layer of security level by requiring you to enter a code from your phone in addition to your password when logging in.
- Keep your software and firmware up to date – Software updates often include security patches that can be helpful to protect your devices and data from known vulnerabilities. Be sure to install updates as soon as they are available on the internet.
- Use a VPN when connecting to public Wi-Fi networks – A VPN encrypts your traffic, making it more difficult for attackers to intercept your data.
- Be careful what you click on and download – Phishing emails and malicious attachments are a common way for attackers to gain access to your network. Be careful about what you click on and download, especially if it comes from an unknown sender.
Educate yourself and your employees about cybersecurity best practices that are going on nowadays. Everyone on your network should be aware of the risks and how to protect themselves.
Some additional tips for securing your network are:
Choose a strong password for your router and change it regularly. You can usually find the default password for your router in the manual or on the manufacturer’s website. You can also enable WPA2-AES encryption for your Wi-Fi network. This is the most secure type of encryption available for home networks.
Use Two-Factor Authentication

Two-factor authentication (2FA) is a security process that requires two distinct forms of identification or authentication from a user before granting them access to a system, account, or application. The goal of 2FA is to enhance security by adding an extra layer of protection beyond just a username and password, which are considered single-factor authentication.
To use two-factor authentication (2FA), you will need to:
Enable 2FA on your account. This process will vary depending on the service you are using, but most services offer detailed instructions on how to do this.
Choose a 2FA method. There are a few different ways to use 2FA, including:
- SMS: This is the most common method, and involves receiving a unique code via text message that you must enter in addition to your password when logging in.
- Authenticator app: This method is more secure than SMS, and involves using a mobile app to generate unique codes that you must enter when logging in.
- Security key: This method is the most secure, and involves using a physical device to generate unique codes that you must enter when logging in.
- Set up your chosen 2FA method. Once you have chosen a 2FA method, you will need to follow the instructions provided by the service you are using to set it up.
- Once you have enabled 2FA on your account, you will need to enter your password and a unique code from your chosen 2FA method every time you log in. This may seem like an extra step, but it is a small inconvenience that can make a big difference in protecting your account from unauthorized access.
Limit Personal Information on Social Media

Limiting personal information on social media means only sharing the information that you are comfortable with being made public. This includes avoiding sharing things like your full name, address, phone number, email address, date of birth, and other sensitive information. It is also important to be mindful of what photos and videos you share, as these can also reveal personal information.
Here are some tips for limiting personal information on social media:
- Review your privacy settings – Most social media platforms have privacy settings that allow you to control who can see your profile and posts. Make sure to review these settings and adjust them to your liking.
- Be selective about what information you share in your profile – You don’t need to share everything about yourself in your profile. Only include information that you are comfortable with being made public.
- Be mindful of what photos and videos you share – Avoid sharing photos and videos that reveal your location, personal information, or sensitive activities.
- Be careful about who you connect with – Only accept connection requests from people you know and trust.
- Be aware of scams and phishing attacks – Social media scammers often try to trick people into sharing their personal information. Be wary of any messages or links from unknown people.
Be Careful When Using Public Wi-Fi

Public Wi-Fi networks can be convenient, but they can also be dangerous. Because anyone can connect to a public Wi-Fi network, it is important to be careful when using one. Here are some tips on how to be careful when using public Wi-Fi:
- Use a VPN Security – A VPN (virtual private network) encrypts your traffic, making it much more difficult for hackers to intercept your data. If you frequently use public Wi-Fi, it is a good idea to invest in a VPN service.
- Avoid entering sensitive information – If possible, avoid entering sensitive information, such as credit card numbers, passwords, and Social Security numbers, when connected to a public Wi-Fi network. If you must enter sensitive information, make sure that the website you are visiting is encrypted. You can tell if a website is encrypted by looking for a lock icon in the address bar and making sure that the URL begins with “https://” instead of “http://”.
- Be careful about what networks you connect to. Not all public Wi-Fi internet is created equal. Some networks may be more secure than others. If possible, avoid connecting to networks that have strange names or that you have never heard of before.
- Be aware of your surroundings. When you are using public Wi-Fi, be aware of your surroundings and who is around you. Avoid using public Wi-Fi in places where you feel unsafe or where there are a lot of people.
Educate yourSelf

There are many resources available to educate yourself about computer security tips to keep your data safe online. Here are a few ideas:
1- Read cybersecurity blogs and articles – There are many websites and blogs that publish articles about cybersecurity best practices. Some good resources include:
- The National Cyber Security Centre (NCSC) website
- The SANS Institute blog
- The Krebs on Security blog
- The CERT/CC blog
2- Take online cybersecurity courses – There are many online courses available that can teach you about cybersecurity fundamentals. Some popular courses include:
- The NCSC’s Cyber Essentials course
- The SANS Institute’s Security Essentials Bootcamp
- The SANS Institute’s Security Awareness Training for Employees
Attend cybersecurity conferences and workshops – There are many cybersecurity conferences and workshops held throughout the year. These events are a great way to learn from experts in the field and network with other professionals.
Conclusion – The conclusion of the article “9 Best Computer Security Tips to Keep Your Data Safe Online” is that by following these nine simple tips mentioned above, you can greatly reduce your risk of falling victim to cybercrime.
